Among the most deadly hazards in the digital sphere is user account takeover. Often without the victim’s knowledge, a hacker takes control of their account. Financial fraud, data theft, or identity abuse could follow from this.
Using phishing prevention, strong passwords, and smart security practices, this guide will coach you through useful actions to stop account compromise and safeguard your users.

🔍 What is a User Account Takeover?
A user account takeover (ATO) happens when an attacker gains unauthorized access to a user’s online account. This could be an email, banking app, e-commerce profile, or even an employee portal.
Common methods include:
- Phishing emails
- Password leaks from data breaches
- Weak or reused passwords
- Malware and keyloggers
Once inside, attackers can steal data, make transactions, or impersonate the user.
✅ Step 1: Encourage Strong Password Practices
A strong password is the first line of defense.
Tips for strong passwords:
- Use a mix of uppercase, lowercase, numbers, and symbols
- Avoid using names, birthdates, or common words
- Minimum 12 characters
Example: T!m3To$ecure2024
Also, encourage the use of password managers to generate and store secure passwords.
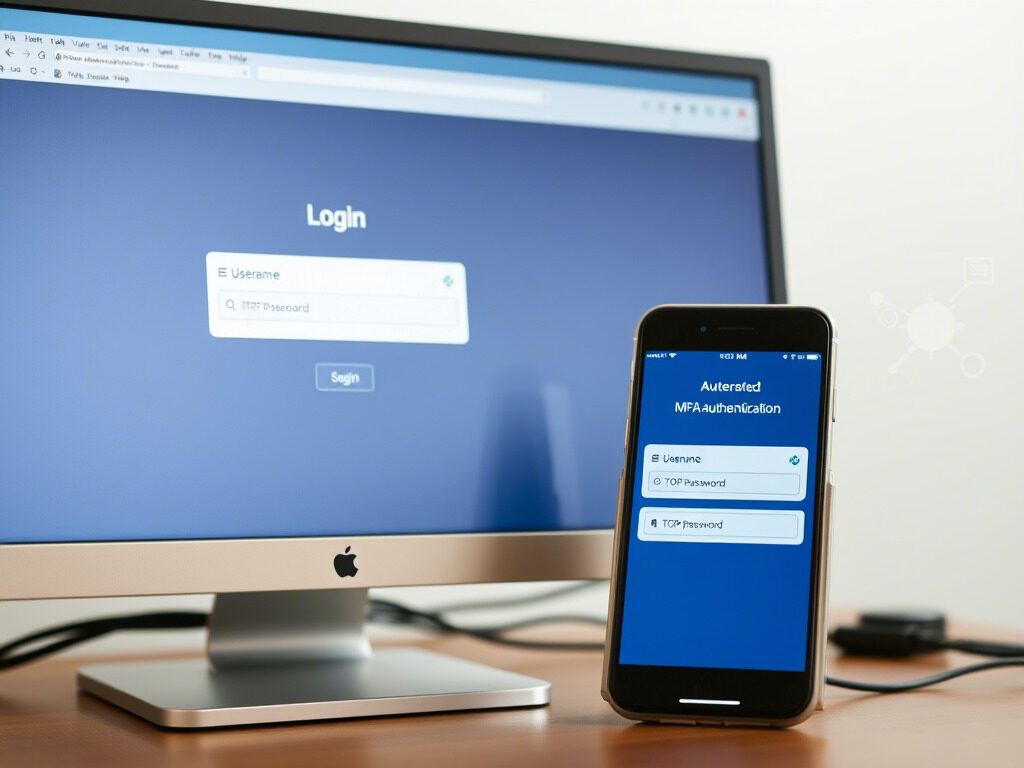
✅ Step 2: Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of protection. Even if the password is stolen, the attacker won’t get in without the second factor (OTP, biometric, authenticator app).
suitable practice:
Use app-based authenticators (like Google Authenticator) instead of SMS-based MFA, which can be vulnerable to SIM swapping.
✅ Step 3: Educate Users on Phishing Prevention
Many account takeovers start with phishing.
Tips for users:
- Never click suspicious links or download unknown files
- Always check the sender’s email address
- Look for HTTPS in URLs before logging in
Hold regular awareness sessions or send short cybersecurity tips via email to keep your team alert.
✅ Step 4: Monitor for Unusual Activity
Use systems that detect:
- Logins from new locations or devices
- Multiple failed login attempts
- Sudden changes in user behavior
Set up alerts for suspicious activity and allow users to view their login history.
✅ Step 5: Enable Account Lockout After Failed Attempts
To block brute-force attacks:
- Lock the account temporarily after multiple failed logins
- Allow recovery through email or phone verification
This adds a safety net against attackers trying to guess passwords.
✅ Step 6: Regularly Update Software and Patch Vulnerabilities
Outdated software can have security gaps. Make sure your platforms, plugins, and apps are up to date with the latest security patches.
Final Thoughts
Account compromise can happen to anyone—but with the right precautions, you can prevent user account takeover and keep your users safe. From using strong passwords to phishing prevention and active monitoring, every step counts.
💼 Want Enterprise-Grade Protection for Your Users?
Let TechNow, the suitable IT Support Agency in Germany, help secure your accounts with advanced authentication, real-time monitoring, and complete user protection.
👉 Contact us today to protect your digital presence from account takeovers.



