One of the main threats to your company is weak passwords. Though they are also easier for hackers to guess, many users select straightforward, memorable passwords. Security depends on enforcing password complexity rules; hence, it is crucial.
This book will teach you how to address password complexity problems, implement appropriate policy enforcement, and assist users in developing robust passwords, safeguarding data and accounts.

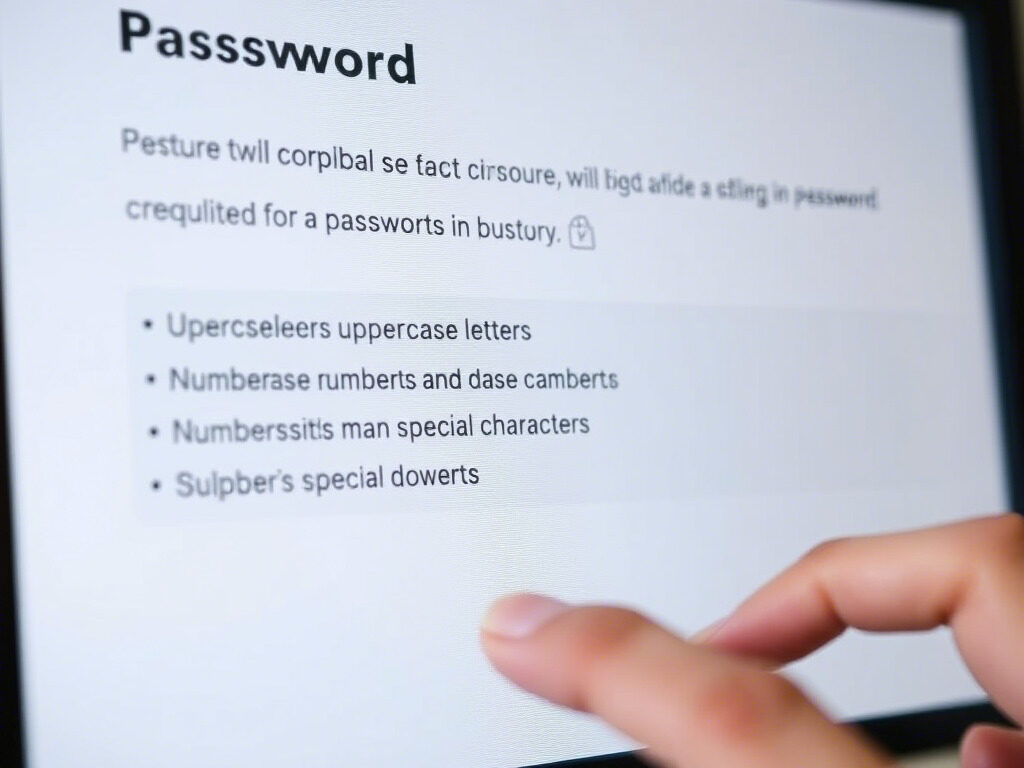
🔍 What Are Password Complexity Requirements?
Password complexity means requiring passwords that are:
- Long enough (usually 8+ characters)
- Include uppercase and lowercase letters
- Have at least one number
- Include a special character (e.g., @, #, $, %)
These rules make passwords harder to guess or crack using brute force.
✅ Step 1: Define a Password Complexity Policy
Set clear rules for what makes a password acceptable.
Recommended policy:
- Minimum 12 characters
- At least 1 uppercase letter
- At least 1 lowercase letter
- At least 1 number
- At least 1 special character
Example: S3cur3!Login2024
This addresses complexity issues right from the start.
✅ Step 2: Enforce Policy in Your System
Windows Group Policy:
- Go to:
Computer Configuration → Windows Settings → Security Settings → Account Policies → Password Policy - Enable:
- “Password must meet complexity requirements”
- “Password must meet complexity requirements”
For Web Applications:
- Use backend validation rules before allowing password creation or change
- Provide real-time feedback with password strength meters
This ensures strong policy enforcement across all platforms.
✅ Step 3: Educate Users About Strong Passwords
Most users don’t understand what a complex password looks like. Provide:
- Examples of strong vs. weak passwords
- Tips on avoiding common patterns (e.g., Password123!)
- Suggestions to use passphrases like Summer$Trip2025!
Educating users reduces resistance and improves compliance.
✅ Step 4: Use Password Strength Meters
A password strength meter helps users visually understand the strength of their chosen password.
It should:
- Show complexity score in real-time
- Warn about weak or reused passwords
- Suggest improvements
This encourages better behavior at the point of entry.
✅ Step 5: Combine Complexity With History and Expiry Rules
Strong passwords are more effective when combined with:
- Password history enforcement (to avoid reuse)
- Expiration rules (e.g., change every 90 days)
- Account lockout policies (after multiple failed attempts)
Together, these create a comprehensive password protection system.
✅ Step 6: Monitor Compliance and Adjust as Needed
Audit password changes regularly:
- Track compliance rates
- Identify users with weak or non-compliant passwords
- Adjust complexity rules if they’re too strict or too lenient
This helps maintain a balance between security and usability.
A key first step in improving the security of your company is enforcing password complexity rules. You lower the danger of breaches and properly safeguard your data by addressing complexity problems, implementing smart policy enforcement, and promoting strong passwords.
💼 Need Help Managing Password Security for Your Organization?
Let TechNow, the suitable IT Support Agency in Germany, help you enforce secure password policies, build user-friendly systems, and stay compliant with the latest standards.
👉 Contact us today and take your password security to the next level.



